The Buzz on Security Solutions
Fully grown MSP's do upkeep and also feedback solutions making use of a centralized console that is attached to your IT facilities. Rates versions for an MSP differ yet typically operate a membership basis. Continue reading to learn more about the fundamentals of using an MSP and what to expect from the relationship. Purchasing a full internal IT division is rather an endeavor.
Per hour solution firms make their money responding to technical issues. In today's globe, the threats of inadequate IT monitoring techniques are severe.
Some Known Details About Collaboration Solutions

If you are taking into consideration working with an MSP, do your research and also make certain that they provide the following solutions: While the above-referenced listing is not extensive, it gives you an excellent idea regarding what you ought to ask when going with the process of selecting an IT took care of provider, like F12 (Video Conferencing).
A per-incident prices model charges a cost per ticket, call, or solution engagement. Usually, per-incident charges are over and over a monthly base fee. All-Inclusive: All-inclusive bundle alternatives resemble "all-encompassing" vacations. It is a detailed all-in-one service for each device and individual under a predictable rate. Like holiday packages, all-encompassing IT bundles have various inclusions as well as exemptions.
Still, work out an important mind when trying to find a taken care of provider in Canada. Make sure to figure out if they are a suitable for your company and if they dedicate themselves to comprehending market advancements. F12 uses handled IT Providers throughout Canada in the following areas:.
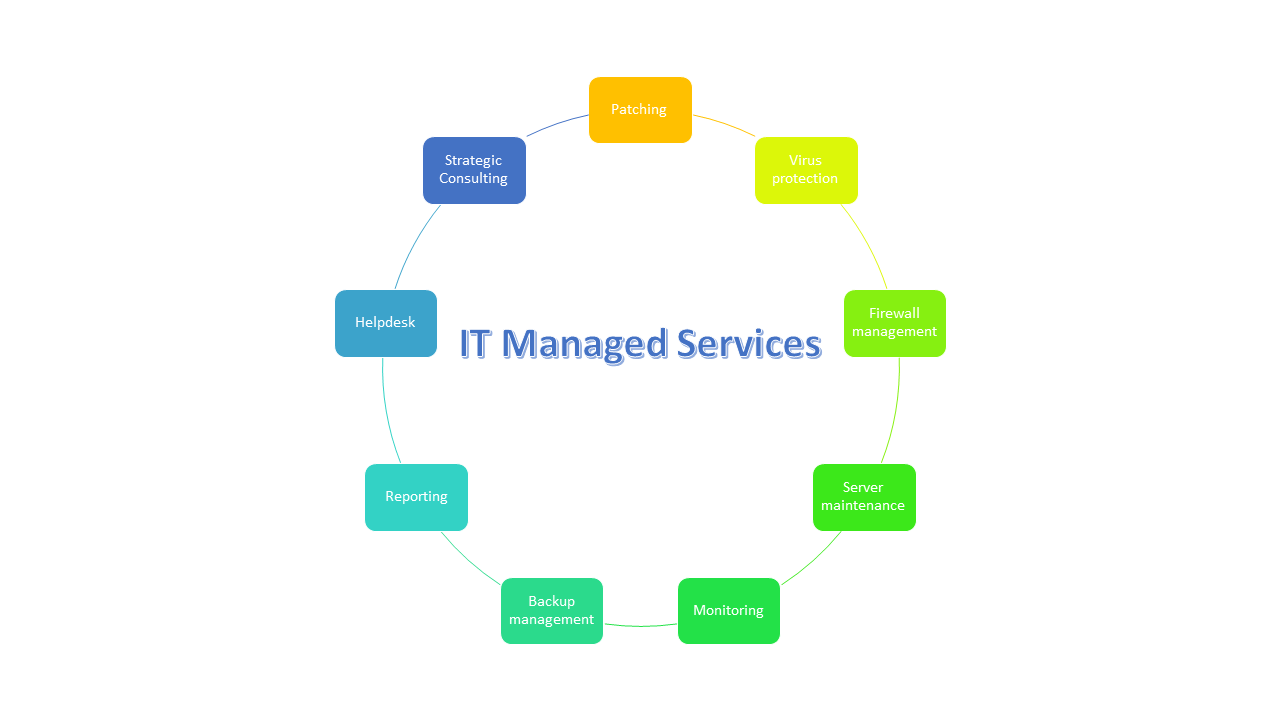
For your very easy glimpse, we have actually separated the handled solutions right into key and also second here, according to their essentiality. End user services can consist of a vast range of solutions, but they regularly fixate the IT helpdesk assistance networks and also treatments that a firm has established for its personnel and customers (Video Conferencing).
The 7-Minute Rule for Collaboration Solutions
Several companies are executing innovation like IT automation, Desktop as a Service, BYOD policies, and more as end-user expectations and also modern technology both create. Taken care of facilities services ought to be thought about when assessing the numerous handled service groups readily available. Think about IT facilities as the lifeblood of any kind of firm; as necessary service operations and regular procedures become much more electronic, the framework that sustains them needs to execute at its finest.
This list demonstrates the range of the his explanation taken care of solution market. They do not require the personnel or sources to build it themselves; they might work with an MSP to satisfy their needs, whether they are small or huge.
Wireless connections will be placed in area by an MSP that offers handled cordless and also mobile computer. Companies that do not have the funds to buy establishing up their own can gain from this service. useful reference Organizations can use this service for interior networks. A range of interaction infrastructures, including Vo, IP (phone over net protocol), information, as well as video, are used by this type of solution.
Mobile working is progressively usual. Lots of people currently function from house or on the move, instead of mosting likely to the workplace daily. Desktop as a Service is the arrangement of a full-featured desktop computer that customers can access from any type of gadget as well as any type of place. Customers are assured a secure connection to their work desktop, plus access to all the programs and data they require, any place they are.
Various other employee are given accessibility to the information as well as data they need to do their jobs, without being able to access the data they do not require. An IDAM service can also aid with conformity, specifically in the age of GDPR. With Handled hosting, your systems and applications are deployed on the MSPs framework, which removes the demand for up-front costs on web servers as well as equipment.
There are numerous topics to resolve! This checklist shows the selection of the taken care of service market. Organizations will certainly gain from having protection for all facets of their IT, many thanks to this. They don't this website need the workers or resources to build it themselves; they may work with an MSP to meet their needs, whether they are little or large.
Security Solutions Fundamentals Explained
Organizations that lack the funds to spend in establishing up their own can profit from this solution. Organizations can utilize this service for inner networks.
Beyond specialized services, team services can likewise be made use of to execute assistance. Offered that problems of differing severity develop every day, IT help is a location that requires unique interest. With your existing staffing method, it could not be feasible to address each of them. Or, present remedies aren't secure over the future.
Managed services encompasses a great deal of IT services and services. Every company has different IT needs, so some may use a Managed Provider for great deals of services while others could make use of just a couple. In either case, took care of solutions can be a really efficient as well as cost-effective IT strategy for services of any kind of dimension.
Mobile working is significantly typical. Great deals of people now work from residence or on the go, rather than going to the workplace daily. Desktop as a Solution is the arrangement of a full-featured desktop computer that individuals can access from any type of device as well as any place. Users are assured a protected link to their work desktop computer, plus access to all the programs and also data they require, wherever they are.
Some Ideas on Security Solutions You Should Know
Other team members are granted access to the information and data they require to do their jobs, without having the ability to access the data they don't need. An IDAM remedy can also assist with conformity, specifically in the age of GDPR. With Handled organizing, your systems and applications are deployed on the MSPs facilities, which eliminates the demand for up front investing on servers and devices.